The home of developer docs at
Cloud Native Security
Discover the APIs, tools and techniques necessary for bringing DevOps practices to the cloud.
Prisma Cloud Enterprise Edition
Prisma Cloud Compute Edition
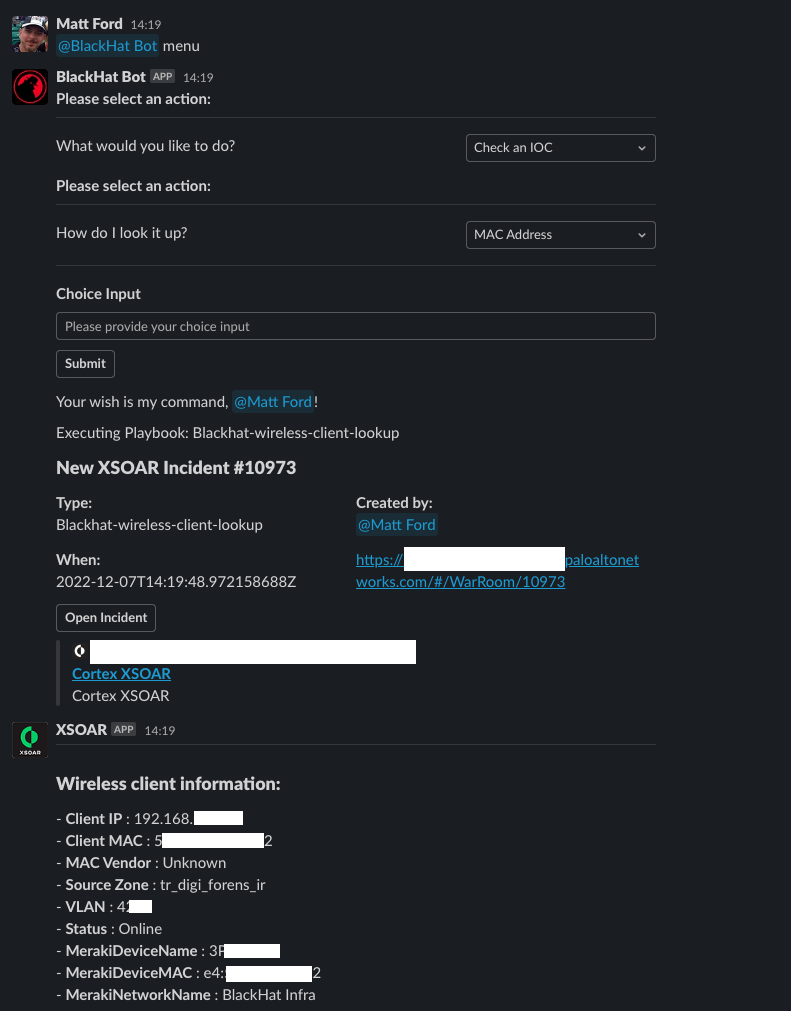
Security Operations
Browse reference docs, tutorials, the XSOAR Marketplace and more.
Cortex XSOAR
Cortex
Network Security
Learn how to make the most of the PAN-OS APIs, SDKs, Expedition, Terraform, Ansible, and more.
PAN-OS
Cloud NGFW
Cortex Data Lake
Cloud-Delivered Security Services
Expedition
Secure Access Service Edge
Discover Prisma SASE APIs, including Prisma Access and Prisma SD-WAN.
Prisma SASE
Prisma Access Configuration
Prisma Access Insights
Prisma SD-WAN
Partner Integrations
Discover technology partner integrations.
Automation
SIEM
Software Firewall deployment with Terraform
Leverage validated Terraform Reference Architectures and Modules for VM-Series and CloudNGFW firewalls for rapid and reliable security in the cloud.
Palo Alto Networks as Code with Terraform
Hashicorp's Terraform is widely used to build and deploy infrastructure, safely and efficiently, with high levels of automation and integration.
Ansible at Palo Alto Networks
The collection of Ansible modules for PAN-OS has been officially certified by the Red Hat Ansible team (list of Ansible certified content) since version 2.12.2.